 Also read:
Also read:
 -What is zombie?
-What is zombie?
 -How do I prevent my computer becoming a zombie?
-How do I prevent my computer becoming a zombie?
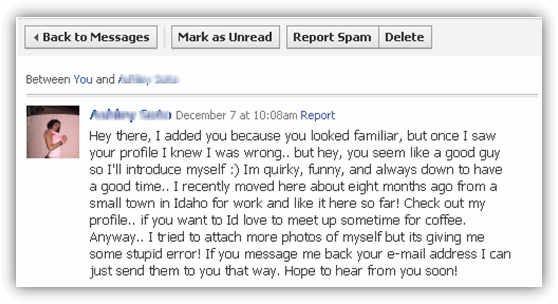
Control What you Share: Spammers collect e-mail addresses from chatrooms, websites, and nowadays especially Social Networking websites. So you got to be very careful about what you share, whom you add as friend, and what you explore on Facebook. Never Scrap your Phone number or home address on facebook, this gives rise yet another big thing “Identity theft”.
Never open unknown emails: Be cautious about opening any attachment or downloading any files from emails you receive. Don’t open an email attachment — even if it looks like it’s from a friend unless you are expecting it or know what it contains. If you send an email with an attached file, include a text message explaining what it is.
Use a Good Antivirus software : and keep it up to date. Look for anti-virus software that recognizes current viruses, as well as older ones. I always Recommend use AVG Free edition – The best (***** from hacker9) And If you have some money to throw use the Premium version.
 Also read:
Also read:  Below are some Examples of Spam emails:
Below are some Examples of Spam emails:
- We carry the most popular medications
- You’ve been sent an Insta-Kiss (phishing scam)
- STEAMY HOT LESBIAN ACTION LIVE ON CAMERA (peddling pornography)
- FREE 60-Second MORTGAGE qualification (identity theft)
- HURRY HURRY hot stock about to go through the roof (email scams)
- You have 14 new pictures (phishing scam)
- Where are you? (peddling pornography)
- Best Sale Prices on iPhones (phishing scam)
- All orders shipped from authorized locations
- V*i*a*g*r*a for cheap.

 zombie is a type of computer virus that infects your PC and causes it to send out spam emails, for a spammer. The spammer controls and uses your pc without you knowing it. Spammers may be using your computer to send unsolicited — and possibly offensive — email offers for products and services. Spammers are using home computers to send bulk emails by the millions. The Zombie is planted on hundreds of computers belonging to unsuspecting third parties and then used to spread E-mail spam and because of this it becomes very difficult to Trace the zombie’s creator. Zombies can also be used to launch mass attack on any company or website.
zombie is a type of computer virus that infects your PC and causes it to send out spam emails, for a spammer. The spammer controls and uses your pc without you knowing it. Spammers may be using your computer to send unsolicited — and possibly offensive — email offers for products and services. Spammers are using home computers to send bulk emails by the millions. The Zombie is planted on hundreds of computers belonging to unsuspecting third parties and then used to spread E-mail spam and because of this it becomes very difficult to Trace the zombie’s creator. Zombies can also be used to launch mass attack on any company or website.
